Thodex - Crypto, Cybersecurity, and Digital Assets News

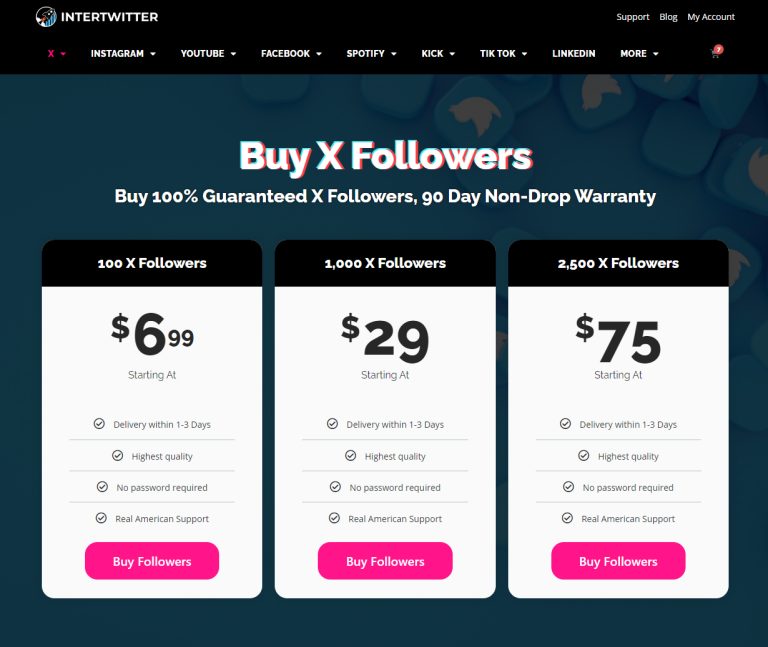
Best Sites To Buy Twitter Followers with Crypto

A Deep Dive into the $7M Abracadabra Finance Hack
SEC Charges HyperFund Co-Founders in $1.7 Billion Crypto Pyramid Scheme
Latest Security News
Latest in Ransomware News
Latest in Crypto Drainers News
Latest in Ai News
Our Sponsors
Thodex, was a cryptocurrency exchange platform based in Turkey, has been a subject of significant attention and controversy within the world of digital finance. Founded by Faruk Fatih Özer in 2017, Thodex initially aimed to provide a secure and user-friendly environment for trading a variety of cryptocurrencies. However, events taking a dramatic turn in April 2021 have since overshadowed its early ambitions, turning Thodex into a cautionary tale about the risks associated with the rapidly evolving cryptocurrency market.
Thodex entered the cryptocurrency scene during a period of explosive growth for digital currencies. Bitcoin, Ethereum, and other cryptocurrencies were gaining widespread attention, and the appetite for investing in digital assets was soaring. Thodex capitalized on this trend by offering a platform that allowed users to trade numerous cryptocurrencies. It attracted a significant user base in Turkey and beyond, partly due to its promotional efforts, which included offering new users a number of free Dogecoins as a sign-up incentive.
The turning point for Thodex came in April 2021, when the platform abruptly halted trading, citing an unspecified investment transaction. This sudden shutdown immediately raised suspicions among its users, many of whom found themselves unable to access their assets. The situation escalated when Faruk Fatih Özer, the founder of Thodex, reportedly left Turkey, leading to allegations of fraud and fears that he had absconded with billions of dollars worth of users’ assets.
Turkish authorities swiftly launched an investigation into Thodex and its executives. Reports emerged suggesting that as many as 391,000 users could have been affected, with the potential losses amounting to hundreds of millions of dollars. The government issued international arrest warrants for Özer and several associated individuals, accusing them of fraud, forming a criminal organization, and laundering money.
The Thodex scandal has had far-reaching implications, not only for the victims of the alleged fraud but also for the cryptocurrency industry in Turkey and globally. It has prompted calls for stricter regulation of crypto exchanges to protect investors from similar incidents in the future. In Turkey, the government has begun to take steps towards establishing a more robust regulatory framework for cryptocurrency trading platforms.
Internationally, the Thodex case serves as a reminder of the risks inherent in the cryptocurrency market. It underscores the importance of due diligence and the need for traders to be cautious when selecting platforms to invest their assets. The incident also highlights the challenges of regulating a rapidly evolving digital finance landscape that transcends national borders.
The Thodex saga is a stark illustration of the volatile and sometimes precarious nature of the cryptocurrency industry. While digital currencies offer the promise of financial innovation and the potential for significant returns on investment, they also come with risks. The Thodex case is a reminder to investors to approach the cryptocurrency market with caution, to thoroughly research the platforms they use, and to be aware of the legal and regulatory environment in which these platforms operate. As the industry continues to evolve, the lessons learned from the Thodex incident will likely influence how cryptocurrencies are traded and regulated worldwide.